The ASEC analysis team has recently discovered the distribution of Cobalt Strike targeting unsecured MS-SQL servers.
MS-SQL server is a typical database server of the Windows environment, and it has consistently been a target of attack from the past. Attacks that target MS-SQL servers include attacks to the environment where its vulnerability has not been patched, brute forcing, and dictionary attack against poorly managed servers.
The attacker or the malware usually scans port 1433 to check for MS-SQL servers open to the public. It then performs brute forcing or dictionary attacks against the admin account, a.k.a. “sa” account to attempt logging in. Even if the MS-SQL server is not open to the public, there are types such as Lemon Duck malware that scans port 1433 and spreads for the purpose of lateral movement in the internal network.

Managing admin account credentials so that they’re vulnerable to brute forcing and dictionary attacks as above or failing to change the credentials periodically may make the MS-SQL server the main target of attackers. Other malware besides Lemon Duck that target MS-SQL server includes CoinMiner malware such as Kingminer and Vollgar.
If the attacker succeeds to log in to the admin account through these processes, they use various methods including the xp_cmdshell command to execute the command in the infected system. Cobalt Strike that has recently been discovered was downloaded through cmd.exe and powershell.exe via the MS-SQL process as shown below.

Cobalt Strike is a commercial penetration testing tool, and it is recently being used as a medium to dominate the internal system in the majority of attacks including APT and ransomware. Malware that has recently been discovered is an injector that decodes the encoded Cobalt Strike inside, and executes and injects the normal program MSBuild.exe.

Cobalt Strike that is executed in MSBuild.exe has an additional settings option to bypass detection of security products, where it loads the normal dll wwanmm.dll, then writes and executes a beacon in the memory area of the dll. As the beacon that receives the attacker’s command and performs the malicious behavior does not exist in a suspicious memory area and instead operates in the normal module wwanmm.dll, it can bypass memory-based detection.
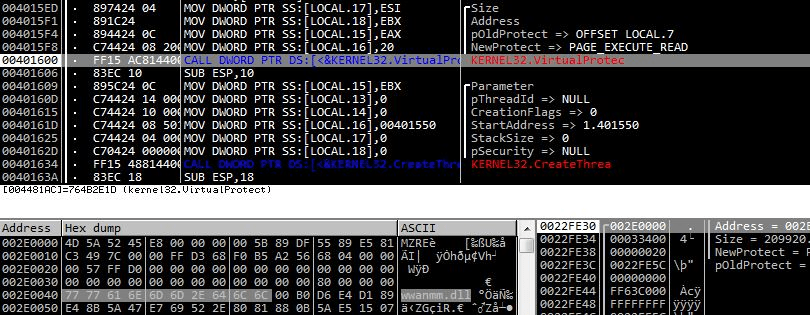
Although it is not certain in which method the attacker dominated MS-SQL and installed the malware, as the detection logs of Vollgar malware that was previously mentioned were discovered, it can be assumed that the targeted system had inappropriately managed the account credentials.
AhnLab’s ASD infrastructure shows numerous logs of Cobalt Strike over the past month. Seeing that the download URLs and the C&C server URL are similar, it appears that most of the attacks were by the same attacker. IOC of Cobalt Strike over the month is shown in the list below.
AhnLab products are equipped with process memory-based detection method and behavior-based detection feature that can counter the beacon backdoor which is used from the Cobalt Strike’s initial invasion stage to spread internally.
[File Detection]
– Trojan/Win.FDFM.C4959286 (2022.02.09.00)
– Trojan/Win.Injector.C4952559 (2022.02.04.02)
– Trojan/Win.AgentTesla.C4950264 (2022.02.04.00)
– Infostealer/Win.AgentTesla.R470158 (2022.02.03.02)
– Trojan/Win.Generic.C4946561 (2022.02.01.01)
– Trojan/Win.Agent.C4897376 (2022.01.05.02)
– Trojan/Win32.CobaltStrike.R329694 (2020.11.26.06)
[Behavior Detection]
– Malware/MDP.Download.M1197
[IOC]
MD5
Cobalt Strike (Stageless)
– ae7026b787b21d06cc1660e4c1e9e423
– 571b8c951febb5c24b09e1bc944cdf5f
– e9c6c2b94fc83f24effc76bf84274039
– 828354049be45356f37b34cc5754fcaa
– 894eaa0bfcfcdb1922be075515c703a3
– 4dd257d56397ec76932c7dbbc1961317
– 450f7a402cff2d892a7a8c626cef44c6
CobaltStrike (Stager)
– 2c373c58caaaca0708fdb6e2b477feb2
– bb7adc89759c478fb88a3833f52f07cf
C&C
– hxxp://92.255.85[.]83:7905/push
– hxxp://92.255.85[.]83:9315/en_US/all.js
– hxxp://92.255.85[.]86:80/owa/
– hxxp://92.255.85[.]90:81/owa/
– hxxp://92.255.85[.]90:82/owa/
– hxxp://92.255.85[.]92:8898/dot.gif
– hxxp://92.255.85[.]93:18092/match
– hxxp://92.255.85[.]93:12031/j.ad
– hxxp://92.255.85[.]94:83/ga.js
Beacon Download URL
– hxxp://92.255.85[.]93:18092/jRQO
– hxxp://92.255.85[.]93:12031/CbCt
Download URL
– hxxp://45.64.112[.]51/dol.exe
– hxxp://45.64.112[.]51/mr_robot.exe
– hxxp://45.64.112[.]51/lion.exe
– hxxp://81.68.76[.]46/kk.exe
– hxxp://81.68.76[.]46/uc.exe
– hxxp://103.243.26[.]225/acrobat.exe
– hxxp://103.243.26[.]225/beacon.exe
– hxxp://144.48.240[.]69/dola.exe
– hxxp://144.48.240[.]85/core.exe
Subscribe to AhnLab’s next-generation threat intelligence platform ‘AhnLab TIP’ to check related IOC and detailed analysis information.
Categories:Malware Information
[…] from this, the cybersecurity researchers have recommended a few security recommendations to mitigate such attacks, and here we have […]
[…] than this, the cybersecurity researchers have really useful a number of safety suggestions to mitigate such assaults, and right here we now […]
[…] operates in the normal module wwanmm.dll, it can bypass memory-based detection,” points out the report by Ahn Lab’s ASEC […]
[…] from this, the cybersecurity researchers have recommended a few security recommendations to mitigate such attacks, and here we have […]
[…] Cobalt Strike Being Distributed to Vulnerable MS-SQL Servers […]
[…] who oversee Microsoft SQL Server databases are being warned to lock down those servers. This comes after security researchers at a South Korean company called ASEC discovered a threat actor is targeting SQL Servers to install the Cobalt Strike beacon. That beacon reports […]
[…] FORRÁS […]
[…] servers,” South Korean cybersecurity company AhnLab Security Emergency Response Center (ASEC) said in a report published Monday.Cobalt Strike is a commercial, full-featured penetration testing […]
[…] than are attacks on other targets.” Criminals continue to misuse Cobalt Strike. Ahn Lab reports that the tool is being distributed to vulnerable MS-SQL servers. BleepingComputer explains that the […]
[…] who oversee Microsoft SQL Server databases are being warned to lock down those servers. This comes after security researchers at a South Korean company called ASEC discovered a threat actor is targeting SQL Servers to install the Cobalt Strike beacon. That beacon reports […]
[…] from this, the cybersecurity researchers have recommended a few security recommendations to mitigate such attacks, and here we have […]
[…] servers,” South Korean cybersecurity company AhnLab Security Emergency Response Center (ASEC) said in a report published […]
[…] Cobalt Strike Being Distributed to Vulnerable MS-SQL Servers […]
[…] these processes, they execute the xp_cmdshell command in the infected system. ASEC researchers explain “Cobalt Strike that has recently been discovered was downloaded through cmd.exe and […]
[…] oversee Microsoft SQL Server databases are being warned to lock down those servers. This comes after security researchers at a South Korean company discovered a threat actor is targeting SQL Servers to install […]
[…] oversee Microsoft SQL Server databases are being warned to lock down those servers. This comes after security researchers at a South Korean company discovered a threat actor is targeting SQL Servers to install […]
[…] oversee Microsoft SQL Server databases are being warned to lock down these servers. This comes after security researchers at a South Korean company discovered a menace actor is concentrating on SQL Servers to put in […]
[…] oversee Microsoft SQL Server databases are being warned to lock down those servers. This comes after security researchers at a South Korean company discovered a threat actor is targeting SQL Servers to install […]
[…] oversee Microsoft SQL Server databases are being warned to lock down those servers. This comes after security researchers at a South Korean company discovered a threat actor is targeting SQL Servers to install […]
[…] crisis in Ukraine may be found here.Criminals continue to misuse Cobalt Strike. Ahn Lab reports that the tool is being distributed to vulnerable MS-SQL servers. BleepingComputer explains that the […]
[…] la empresa de ciberseguridad de Corea del Sur AhnLab Security Emergency Response Center (ASEC) dijo en un informe publicado el […]
[…] », la société sud-coréenne de cybersécurité AhnLab Security Emergency Response Center (ASEC) mentionné dans un rapport publié […]
[…] who oversee Microsoft SQL Server databases are being warned to lock down these servers. This comes after security researchers at a South Korean company called ASEC discovered a risk actor is focusing on SQL Servers to put in the Cobalt Strike beacon. That beacon studies […]
[…] who oversee Microsoft SQL Server databases are being warned to lock down those servers. This comes after security researchers at a South Korean company called ASEC discovered a threat actor is targeting SQL Servers to install the Cobalt Strike beacon. That beacon reports […]
[…] who oversee Microsoft SQL Server databases are being warned to lock down these servers. This comes after security researchers at a South Korean firm known as ASEC discovered a possibility actor is focusing on SQL Servers to install the Cobalt Strike beacon. That beacon […]
[…] who oversee Microsoft SQL Server databases are being warned to lock down those servers. This comes after security researchers at a South Korean company called ASEC discovered a threat actor is targeting SQL Servers to install the Cobalt Strike beacon. That beacon reports […]
[…] who oversee Microsoft SQL Server databases are being warned to lock down those servers. This comes after security researchers at a South Korean company called ASEC discovered a threat actor is targeting SQL Servers to install the Cobalt Strike beacon. That beacon reports […]
[…] who oversee Microsoft SQL Server databases are being warned to lock down these servers. This comes after security researchers at a South Korean company known as ASEC found a threat actor is concentrated on SQL Servers to set up the Cobalt Strike beacon. That beacon […]
[…] Cobalt Strike being distributed to vulnerable MS-SQL servers […]
[…] Microsoft SQL Server databases are being warned to fasten down the ones servers. This comes after safety researchers at a South Korean corporate found out a danger actor is concentrated on SQL Servers to put in […]
[…] are many publications around database attacks and breaches. Recently researchers found that attacks are using Cobalt Strikes’ beacon to get control over MS-SQL servers. This can […]
[…] who oversee Microsoft SQL Server databases are being warned to lock down those servers. This comes after security researchers at a South Korean company called ASEC discovered a threat actor is targeting SQL Servers to install the Cobalt Strike beacon. That beacon reports […]
[…] are many publications around database attacks and breaches. Recently researchers found that attacks are using Cobalt Strikes’ beacon to get control over MS-SQL servers. This can […]
[…] who oversee Microsoft SQL Server databases are being warned to lock down those servers. This comes after security researchers at a South Korean company called ASEC discovered a threat actor is targeting SQL Servers to install the Cobalt Strike beacon. That beacon reports […]
[…] [ASEC Blog] Cobalt Strike Being Distributed to Vulnerable MS-SQL Servers– [ASEC Blog] Cobalt Strike Being Distributed to Vulnerable MS-SQL Servers (2)– [ASEC […]
[…] [ASEC Blog] Remcos RAT Being Distributed to Vulnerable MS-SQL Servers– [ASEC Blog] Cobalt Strike Being Distributed to Vulnerable MS-SQL Servers– [ASEC Blog] Cobalt Strike Being Distributed to Vulnerable MS-SQL Servers […]
[…] servers,” South Korean cybersecurity company AhnLab Security Emergency Response Center (ASEC) said in a report published […]
[…] servers,” South Korean cybersecurity firm AhnLab Safety Emergency Response Middle (ASEC) stated in a report printed […]
[…] method discovered by the South Korean cybersecurity firm entails the use of CLR stored procedure to install the malware in MS SQL servers using the xp_cmdshell command, which spawns a Windows command shell […]
[…] method discovered by the South Korean cybersecurity firm entails the use of CLR stored procedure to install the malware in MS SQL servers using the xp_cmdshell command, which spawns a Windows command shell […]
[…] gaining unauthorized access, the hackers implanted the payload into a legitimate Windows dll (wwanmm.dll) to avoid memory-base […]
[…] are many publications around database attacks and breaches. Recently researchers found that attacks are using Cobalt Strikes’ beacon to get control over MS-SQL servers. This can […]